Preface. I’ve been reading about cyber threats since 2007, and a problem still true today is that the government can do nothing except a few puny regulations here and there for the most part, since critical infrastructure like energy and finance are in PRIVATE hands.
But across all of the 16 critical infrastructures that depend on the electric grid being up, capitalist companies own them and care only about good financial results the next quarter. Cybersecurity costs a lot of money and reduces profitability, making it low priority for many companies. According to this latest 2022 report, this is still true (though of course the DOE didn’t put it this bluntly).
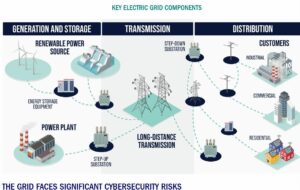
Another problem is that before the internet it couldn’t be hacked. But now with covid-19 and ease of monitoring and operations, power stations, dams are on the internet and hackable.
Due to ransomware, energy is one of the most profitable sectors to attack. Malicious cyber actors understand that the priority for availability for energy systems makes these system owners more likely to pay quickly to restore service, rather than face days, weeks, or months of downtime to restore from backups. A January 2022 report from a commercial cyber threat analysis company found that 20% of ransomware attacks in the third quarter of 2021 targeted utilities, and utilities are the second most-targeted critical infrastructure sector.
This is just one of the reports on supply chains essential for “America’s Strategy to Secure the Supply Chain for a Robust Clean Energy Transition”. The other reports are on: carbon capture materials • electric grid including transformers and high voltage direct current (HVDC) • energy storage • fuel cells and electrolyzers • hydropower • neodymium magnets • nuclear energy • platinum group metals and other catalysts • semiconductors • solar photovoltaics (PV) and • wind.
These reports are dishonest in that they don’t even mention many of them are still in development, far from commercial. That they can’t scale up. Numerous obstacles are left out. Assumptions we can make a lot of stuff in the US and not be dependent on hostile nations (especially China).
I left a good deal about Artificial Intelligence, data and more, read the 33 page document if you’d like to know more.
Alice Friedemann www.energyskeptic.com Author of Life After Fossil Fuels: A Reality Check on Alternative Energy; When Trucks Stop Running: Energy and the Future of Transportation”, Barriers to Making Algal Biofuels, & “Crunch! Whole Grain Artisan Chips and Crackers”. Women in ecology Podcasts: WGBH, Jore, Planet: Critical, Crazy Town, Collapse Chronicles, Derrick Jensen, Practical Prepping, Kunstler 253 &278, Peak Prosperity, Index of best energyskeptic posts
***
DOE (2022) Cybersecurity and digital components. Supply chain deep dive assessment. U.S. Department of Energy Response to Executive Order 14017, “America’s Supply Chains”. www.energy.gov/policy/supplychains
All digital components in U.S. energy sector systems are vulnerable and may be subject to cyber supply cha in risks stemming from a variety of threats, vulnerabilities, and impacts. This includes digital components in all systems within the Energy Sector Industrial Base (ESIB), namely those systems operated by asset owners across different energy subsectors (e.g., electricity, oil and natural gas, and renewables) and the systems operated by a worldwide industrial complex with capabilities to perform research and development and design, produce, operate, and maintain energy sector systems, subsystems, components, or parts to meet U.S. energy requirements. Supply chain risks for digital components including software, virtual platforms and services, and data have grown in recent years as increasingly sophisticated cyber adversaries have targeted exploiting vulnerabilities in these digital assets. Supply chain risks for digital components in energy sector systems will continue to evolve and likely increase as these systems are increasingly interconnected, digitized, and remotely operated.
Supply chain risks for digital components in critical infrastructure systems have grown in recent years as increasingly sophisticated cyber adversaries have targeted exploiting vulnerabilities in these digital assets. In its Annual Threat Assessment for 2021,the U.S. Intelligence Community noted, “During the last decade, sta te sponsored hackers have compromised software and IT service supply chains, helping them conduct operations—espionage, sabotage, and potentially prepositioning for warfighting.” 1 In a 2018 alert,2 the Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI) highlighted growing cybersecurity concerns and several cyber attacks specifically targeting the energy sector using, among other exploits, cyber supply chain vulnerabilities in trusted third-party suppliers with less secure networks.
[The report then lists five major attacks on the energy sector in Ukraine, Saudi Aramco, Colonial Pipeline and SolarWinds in the U.S., Vestas wind turbines]
Reliance on Foreign Suppliers
Cyber components in energy sector systems are globally sourced in an increasingly fragmented and dynamic digital supply chain. Software for IT and OT systems is increasingly developed in foreign countries where skilled labor pools exist, internet connectivity is available, and lower wages are common. Cyber supply chain risks stem from several conditions related to this reliance on lower cost foreign suppliers of software, which may be designed, developed, manufactured, maintained, or supplied by persons owned or controlled by, or subject to the jurisdiction or direction of, a foreign adversary.
Under these conditions, software and firmware can be developed by untrusted individuals who could insert malicious code that is difficult to detect due to the size and complexity of these systems. Additionally, software, firmware, and datasets can be developed in adversary nations that practice ubiquitous collection of all digital information on networks that transit their territory, which creates an opportunity to insert malicious code or otherwise interfere in software developed within their borders or compromise the integrity of datasets.
Similarly, virtual platforms and services that are hosted in datacenters resident in some adversary nations are subject to the same types of collection and interference. The compromise of the SolarWinds Orion platform is the most serious recent example that demonstrates that any software maintenance supply chain is vulnerable to manipulation at the hands of a strategic, well-resourced nation-state operation
Software code is assembled from parts and pieces of older code from a huge variety of original and indirect sources with differing levels of quality and of integrity assurance. Consequently, it is extremely difficult to track the provenance and source of all code in software and digital components in order to illuminate and manage the risk of supply chain compromise by ensuring that the code stems from trustworthy sources.
While increasingly ubiquitous due to its convenience and efficiency, open source software is an increasing area of concern from a cybersecurity standpoint. Open source software frequently comes without a clear provenance and is often not consistently maintained (for example, with security updates), creating cyber supply chain risks. Cyber adversaries actively use open source code libraries to disperse malicious code to unsuspecting software developers
Mergers and Acquisitions. Acquisitions of technology companies often result in re-branding and integration of digital components into larger product suites, obscuring the provenance of these subcomponents. M&A activity can result in rapid changes in foreign ownership and control that are difficult to determine, much less track, and adversary nations often actively seek to obfuscate foreign ownership and control. Assumption of control of a technology company often means access to all source code, sensitive current and historical customer data, and continuing access to customer systems for maintenance
Concentrated Cyber Risk. Some attributes of software and with high strategic value include software that: is broadly used or present in a high percentage of system s; accesses network credentials as part of its normal operations; runs below the application layer and is less visible to network managers; and frequently goes unpatched for long periods of time. The fact that many internal critical infrastructure systems and components are dependent on some form of servicing (i.e., remote or direct upgrades, patches, etc.) increases the attack surface for these components. Within the past five years, significant research has demonstrated that malicious, covert manipulation of datasets used in AI training can cause significant and nearly impossible-to-detect system failures.
The trend towards remote operation has been greatly accelerated in the past year by the global pandemic. The imperative for worker safety has accelerated asset owner investments in remote operation technologies.
