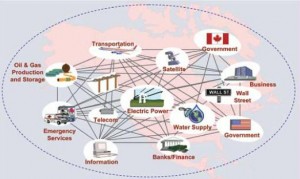
An Attack on Energy Infrastructure would affect all other Infrastructure
I should consolidate my many posts on cyber attacks, EMPs, and other ways the electric grid could come down, but our dependencies are just so widespread that I don’t want to bury gather the myriad ways our lives depend on electricity in a gigantic post no one will read. The grid will come down eventually though, because it is still nearly two-thirds powered by FINITE coal and natural gas power plants, and as I explain in posts in category Energy Storage, there is no way to store electricity long enough to keep the grid up.
Developments in digital information and telecommunications dramatically increased inter-dependencies among U.S. critical infrastructures. Each depends on others to function successfully. Disruptions in a single infrastructure can generate disturbances within others over long distances and amplify the effects of a disruption. The energy infrastructure provides essential fuel to all of the other critical infrastructures, and in turn depends on the Nation’s transportation, information technology (IT), communications, finance, and government infrastructures. Over time cyber/IT dependencies have increased. Energy control systems and the information and communications technologies on which they rely play a key role in the North American energy infrastructure. They are essential in monitoring and controlling the production and distribution of energy. They have helped to create the highly reliable and flexible energy infrastructure in the U.S.
Alice Friedemann www.energyskeptic.com Author of Life After Fossil Fuels: A Reality Check on Alternative Energy; When Trucks Stop Running: Energy and the Future of Transportation”, Barriers to Making Algal Biofuels, & “Crunch! Whole Grain Artisan Chips and Crackers”. Women in ecology Podcasts: WGBH, Jore, Planet: Critical, Crazy Town, Collapse Chronicles, Derrick Jensen, Practical Prepping, Kunstler 253 &278, Peak Prosperity, Index of best energyskeptic posts
***
Energy Infrastructure
Electric Grid – see “What would happen if the electric grid was cyberattacked?”
Energy distribution, equipment, refineries, and so on rely on SCADA and other computer systems that could be cyber (and physically) attacked. In fact, the entire oil refining process depends on computers, from computer operation stations with digital proximity switches and other devices to operate valves and switches, monitor critical parameters, and provide automatic shutdown procedures.
Without a stable energy supply, health and welfare are threatened and the U.S. economy cannot function.
Petroleum
- 525,000 crude oil producing wells
- 30,000 miles of oil gathering pipelines
- 51,000 miles of crude oil pipeline
- 116,000 miles of product pipeline
- 150 petroleum refineries
- 1,400 petroleum terminals
Natural Gas
- 478,562 gas production and condensate wells
- 20,215 miles of gathering pipes
- 550 gas processing plants
- 319,208 miles of interstate and intrastate distribution pipelines
- 399 underground storage facilities
- 1,200,000 miles of pipelines to distribute natural gas to homes and businesses
How hard would it be to attack (energy) infrastructure?
STATEMENT OF JAMES A. LEWIS, DIRECTOR AND SENIOR FELLOW, TECHNOLOGY AND PUBLIC POLICY PROGRAM, CENTER FOR STRATEGIC AND INTERNATIONAL STUDIES
You can download the tools that will find critical infrastructure vulnerabilities easily off the internet. I did it last week and I toyed around with it and found 6,000 vulnerable networks Combine these reconnaissance tools with the attack tools available in the cyber crime black market, and someone with good hacking skills—and there are many in these groups—could attack the poorly-defended critical infrastructures that are found in this country.
As cyber attack capabilities become commoditized, the temptation for these politically motivated groups to use them against vulnerable U.S. targets will increase.
The number of nations seeking to acquire cyber attack capabilities is growing rapidly— cyber attack is becoming a standard element in military planning. A more troubling development is that new classes of opponents are seeking the ability to launch cyber attacks. These new classes of opponents will not be as easily constrained. They are more likely to use cyber attack and all evidence suggests that we have nothing in the way of adequate defense. We simply do not take the threat of cyber attack seriously.
The area of greatest concern is in the diffusion of the ability to attack critical infrastructure, to less responsible and less deterrable actors who may calculate that it is in their interest to launch a cyber attack against the United States. Attack capabilities could spread if private hackers to independently discover the techniques currently possessed by governments. Some members of the hacker community have amazing capabilities. Another way attack capabilities could spread would be for hackers who are government proxies in Russia and China to ‘‘commercialize’’ the skills and tools they have been provided for official purposes. These proxies receive training and support from military and intelligence agencies. They also participate in the cyber crime black markets. The flow from government agencies to proxies to the black market is likely.
Unfortunately, even private hackers can exploit freely available information on vulnerabilities and penetration techniques to attack many commercial networks and the critical infrastructure connected to them. Why use an advanced attack like Stuxnet when a simple attack will work so well? There are tools that allow anyone to scan the internet to find unprotected digital devices at critical infrastructure facilities that connect control systems to the internet. You can scan for devices that are improperly configured, devices such as wireless routers that come from the manufacturer with the password set as ‘‘password.’’ It does not take a mastermind to break into such systems. These tools are widely available. Informal tests using these tools can find several thousand insecure connections in the United States on any given day. They provide a ‘‘consumer version’’ of the cyber reconnaissance an advanced power would carry out in planning an attack against the United States. Combine these publicly available reconnaissance tools with attack tools available on the cyber crime black market, and anyone with sufficiently advanced hacking skills will be able to attack poorly defended critical infrastructure or other commercial targets.
We must also consider motivation and intent, in addition to capability. The few nations that currently possess advanced cyber attack capabilities are deterred by American military force or they are our allies. Most cyber criminals only engage in actions that generate income. Attacking critical infrastructure does not generate income unless extortion is involved (by threatening to disrupt services if the criminal is not paid). Cyber criminals have no motive to launch a cyber attack unless they are acting as government proxies or unless they have been hired as mercenaries. This is where the nexus between the diffusion of attack capabilities and intent become important. There are countries and groups that would like to attack the United States and are not as deterrable as our current adversaries. As nations and hackers develop more sophisticated attack capabilities and as sophisticated attack tools become available on the cyber crime black market, the threat of attack is increasing.
We know that two countries hostile to the United States are developing cyber attack capabilities. North Korea has been pursuing cyber capabilities for more than a decade but the backwardness of its economy has so far limited its success. North Korea lacks easy access to advanced technologies. Its tightly controlled population is an unlikely source of hackers, as North Koreans do not have the independence and internet access hackers need to thrive. Technological backwardness and political culture are major obstacles to developing strong hacking capabilities, but, as with nuclear weapons, if North Korea is able to support sustained investment in cyber attack capabilities and find some outside support, it will eventually acquire them. North Korea’s erratic behavior suggests it will use cyber attacks against South Korea, Japan, or U.S. forces in Korea, should it succeed in its long quest to obtain a cyber attack capability.
Iran is a more troubling case. Iran has also been pursing the acquisition of cyber attack capabilities for several years. Iran has been for many years willing to attack U.S. forces and embassies in the region, and FBI Director Mueller stated in recent testimony that Iran is more willing to carry out attacks inside the United States. Statements by Iranian officials show that they believe that the United States, along with Israel, was responsible for the Stuxnet attacks and suggest that they believe they would be justified in retaliating in kind. Iran’s attack capabilities are still limited but they have probed Israeli networks in what appear to be tests. Iranian hackers have greater access to the internet and to the cyber black market than North Korea, suggesting that their development of cyber capabilities will be more rapid.
Iran, even more than North Korea, could miscalculate the costs of a cyber attack against the United States. Iran has groups that it sponsors, like Hezbollah, that it has used in the past to attack Americans. The Iranians may believe that these proxies will make it difficult for the United States to attribute an attack and this will reduce their perceptions of the risk of a cyber attack on American targets.
STATEMENT OF GREGORY C. WILSHUSEN, DIRECTOR, INFORMATION SECURITY ISSUES, GOVERNMENT ACCOUNTABILITY OFFICE
We have also identified vulnerabilities and industrial control systems that monitor and control sensitive processes and physical functions supporting the Nation’s critical infrastructures. Federal agencies continue to report an increasing number of cybersecurity incidents. Over the past 6 years, the number of incidents reported by Federal agencies to US–CERT has risen nearly 680 percent, to almost 42,900 in fiscal year 2011. These incidents include unauthorized access and improper use of computing resources and the installation of malicious software on systems. Reported attacks and unintentional incidents involving Federal, private, and critical infrastructure systems occur daily and demonstrate that their impact can be serious.
Other vulnerable infrastructure
These are all essential for the functioning of an economy. Destruction or compromise of any of these systems/services would be debilitating either directly or through cascading effects.
- Agriculture
- Banking and Finance
- Chemical and Hazardous materials
- Commercial assets
- Dams
- Defense industrial base
- Emergency services
- Energy
- Information technology
- National monuments and icons
- Nuclear power
- Organizations
- Postal and shipping
- Public Health
- Telecommunications
- Transportation
- Water and water treatment systems
August 2, 2013. Tom Simonite. Chinese Hacking Team Caught Taking Over Decoy Water Plant. A hacking group accused of being operated by the Chinese army now seems to be going after industrial control systems. TechnologyReview
References
CYBERSECURITY. Threats Impacting the Nation. April 24, 2012. Subcommittee on Oversight, Investigations, and Management, Committee on Homeland Security, House of Representatives.
Energy Sector-Specific Plan. An annex to the National Infrastructure protection plan. 2010. United States Department of Energy & Homeland Security.
Spellman, Frank. 2010. Energy Infrastructure Protection and Homeland Security
Related articles (links to some of these may be broken but most of them are still here)
- Cyber Attacks an unprecedented threat to U.S. National Security, a review of U.S. House of representatives March 21, 2013 session on Cyber attacks
- Will we go out with a whimper instead of a bang? Cyberwar more likely than nuclear war
- It’s only a matter of time before Cyber Terrorists launch attacks
- Military Threats: Peak oil, population, climate change, pandemics, economic crises, cyberattacks, failed states, nuclear war.
- China is working on cyber attacks of our infrastructure and stealing secrets
- Emergency drill: Cyberattack on electric grid. Wald, Matthew L. August 16, 2013. As Worries Over the Power Grid Rise, a Drill Will Simulate a Knockout Blow. New York Times.
- Cyber Attack Methods. Who are the cyber attackers?
- Energy infrastructure cyberattack targets
- Actual cyber attacks
- House hearing: protecting small businesses against cyber-attacks 2013
- S. House: Iranian cyber threat to the United States
Electric Grid
- Electric grid large power transformers take up to 2 years to build. Excerpts from Department of Energy “Large Power transformers and the U.S. electric grid”.
- EMP effect on electrical transformers. A review of Dr. Jeff Masters 2009 “A future Space Weather catastrophe: a disturbing possibility”.
- The EMP Commission estimates a nationwide blackout lasting one year could kill up to 9 of 10 Americans through starvation, disease, and societal collapse
- Electromagnetic pulse threat to infrastructure (U.S. House hearings) from the transcripts of the 2012 and 2014 hearings
- Chip Fab Plants need electricity 24 x 7. The electric grid needs chips. The Financial system needs both.
- Electric Grid Overview
- Terrorism and the Electric Power Delivery System. National Academy of Sciences. Excerpts from the National Academy of Science 2012 “Terrorism and the Electric Power Delivery System” & 2013 “The Resilience of the Electric Power Delivery System in Response to Terrorism and Natural Disasters”
- What would happen if the electric grid was cyberattacked?